This section describes how WebSTAR handles HTTP connections, including techniques for tracking user interaction; realm and web user security processing of URLs; procedure for serving a requested file or other data; and how WebSTAR responds to errors.
The HyperText Transfer Protocol (HTTP) defines how a Web server handles connections. Unlike some protocols, HTTP opens connections only for as long as needed to transfer the requested data. The connections are then closed immediately. Even "persistent" connections do not create a long-term link between the server and the client: as soon as the data is transferred, the connection is closed.
The WebSTAR Web server also supports the HTTPS (secure) protocol. It works like HTTP, but the data is encrypted before being transmitted. For more information, see SSL Web Security .
This method of handling connections has a few implications for the administrator of a Web server. First, there is no way for WebSTAR to keep track of where a connection leads. So, if a browser requests data from your server, there is no way for the WebSTAR Web server to track which links are followed within that data, because the connection is closed once the original data is returned.
In addition, each separate element in a page requires its own connection. For example, a page of text requires one connection to download. If that page contains a graphic, another connection is required. Therefore, connection information is not necessarily a reliable way of analyzing a server's activity. For example, if you have a server with 5,000 connections a day serving a text document and you add a graphic to that document, your server will suddenly report serving 10,000 connections a day, simply because it's serving an additional graphic each time.
By using the Persistent Connections feature of WebSTAR, the server can hold open a single connection and use it to transmit multiple files, thus reducing the overhead of setting up and closing connections.
see Use DNS for Server and Client Lookups .
As described above, HTTP closes connections as soon as the requested data is served. However, there are many good reasons why you would want to keep track of a person as they go through your site, and after they leave and come back. For example, you may want to suggest related pages, track online tests, show them what's new since the last time they looked at the site, or track the choices on a store.
There are a number of approaches to tracking viewers to your site:
http://search.netscape.com/assist/security/faqs/cookies.html
http://software.apple.com/webobjects/
http://www.starnine.com/extendingwebstar.html
You can also track people viewing your site by viewing your log files (see Web Server Logging ). For statistics and analysis, you may want to use a log analyzer. Many of them will let you learn how people travel within your site and which elements are the most effective. Many log analysis programs are available: see the Extending WebSTAR pages for links.
The Web browser (client) software is responsible for constructing the full URL for a document, which contains the server's hostname and possibly a path to the folder or file containing the desired data.
Once the WebSTAR Web server receives the URL and has routed it to the correct host, it has to find the data. Some URLs are for files, others for CGIs and Plug-Ins, but the process is very much the same.
For example, this is a full URL to an HTML document:
http://www.domain.com/widgets/bluewidget.html
The client machine looks up the domain in the DNS registry, and locates the IP address of your WebSTAR server machine.
By default, WebSTAR analyzes URLs relative to its own position on the disk. Therefore, the WebSTAR root folder for the WebSTAR web server is the folder in which the server application resides. A root URL is just the name of your host, which will bring up your default or index file in the root folder:
http://www.domain.com
If you are serving several hosts, the root folder for each of those hosts is the folder that you designate in the Virtual Hosts list. WebSTAR will respond to the URL relative to that folder for that virtual host, so it will bring up the index or default file in that folder.
For more information on virtual hosts, see below and Routing to Virtual Hosts .
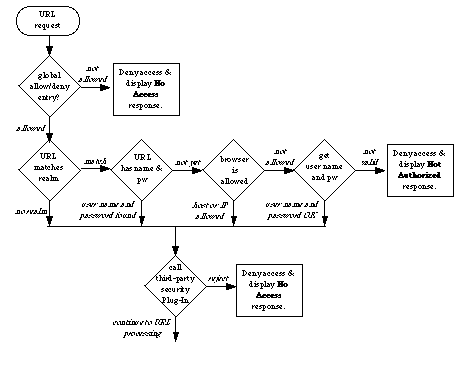
When the WebSTAR server receives an incoming URL, it performs the steps described below.
See Security Realms .
From here on, the WebSTAR web server works on the data path elements of the URL. In this example:
http://www.domain.com/widgets/bluewidget.html
widgets/bluewidget.html
If the URL points to an alias, WebSTAR will use the suffix of the alias: it will not use the suffix of the original file.
For more information, see Suffix Mapping .
http://www.domain.com/widgets
http://www.domain.com/widgets/
If the requested data was not found, or the person requesting it was denied access to a security realm, WebSTAR will return one of the specified error messages.
To designate a special error file or use a third-party CGI or Plug-In to respond to these errors, redirecting the browser to another file or giving a more useful error message, see Default Names .
If you are using Virtual Hosting, each host can have separate error message settings. See Virtual Host Options .
If a browser sends a URL for a file that does not exist, WebSTAR will send back a standard error message. The default behavior is to send the file Error.html , installed in the root folder, which has a "File Not Found" error message.
You can edit that file in your favorite HTML editor, to make it more useful to people accessing your site. For example, you can add a site map, a list of the most important links on your site, or a search form for your site--all tools to make it easier for your visitors to get back on track. You should also add the webmaster email address and consider providing a contact phone number as well.
You can use the Global option in the Allow/Deny interface to deny a browser access to the entire host, according to the browser machine's host name, domain name or IP address. If you do so, and a browser from that domain attempts to access the server, they will get the No Access error page.
The default behavior is to send the file NoAccess.html from the root folder, with an "Access Denied" message. You can edit that file in your favorite HTML editor to explain how they can get access to the host, or replace the file entirely.
When a browser tries to access a secure realm, but the user does not enter a valid user name and password, the web server will return the pre-set Not Authorized error message. You cannot edit this message in HTML.
When WebSTAR gets a URL, it must first make sure that the browser machine is allowed to access that particular data. Only once it has checked all security options will it go on to find and serve the data, as described below in WebSTAR URL Processing .
For information on using this security, see Allow/Deny .
After a denial, the User Name and Password dialog will always appear in the browser, even if there is no User entry associated with a realm.